- User logs into your system.
- Your backend provides your frontend code with a Cello JWT token.
- Your frontend code initializes the Referral Component with the token.
Generating the token
Keep your credentials safe. Never generate a token or store your secret on the client side!
- Your Cello credentials: productId and product secret
- A productUserId that uniquely identifies the logged-in user
- A token signing library for your tech stack of choice. A good variety can be found in the JWT community
Credentials
You will require both productId and product secret to generate tokens for your users. You can find these in your Cello Portal: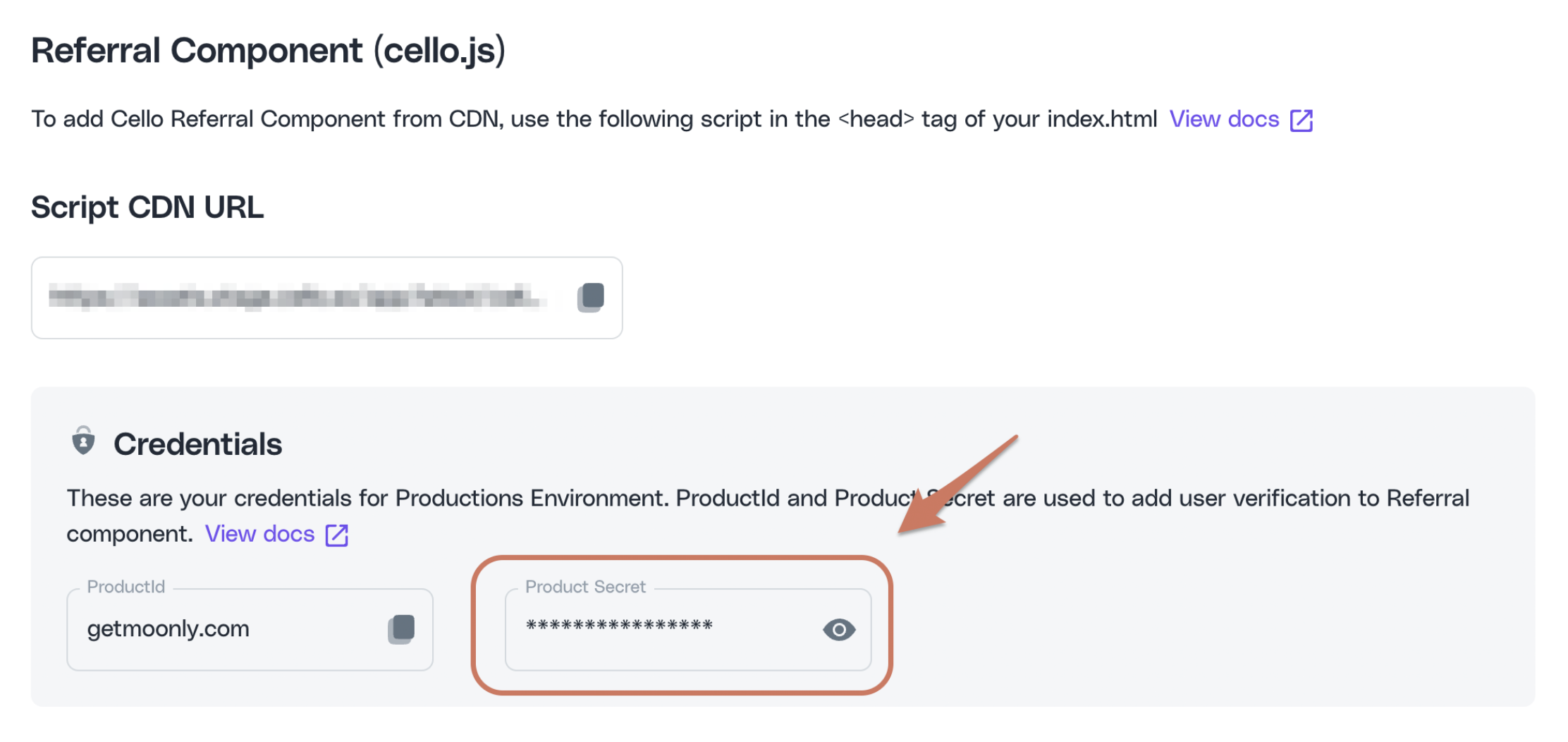
User identity
Cello requires a productUserId - a unique user identifier to be passed when initializing the Referral Component. This can be a user id that you already use to identify users in your product. It can also be any other new unique identifier you generate - the main requirement is that it is unique per user accross your application.JWT signing library
Regardless of the signing library you choose, make sure you use theHS512 signing algorithm:
Token generation
Token payload attributes:Identifier of the product your users will refer
Your logged-in user’s unique identifier within your system
A token issuing Unix timestamp. Example:
1661876739Original signup date of the user. This helps to improve accuracy for auto-attributions.
List of organizations the user is assigned to. This is required to enable automatic attribution when referrals are based on organizations. More information.
Note that some libraries do not require you to pass
iat in the payload and default to the current time if you don’t.Example
Example of token generation in a NodeJS backend with JavaScript:Creating a JWT token should always be done in your backend code and not in the browser!
Using the token
Finally, provide the server side-generated token in thetoken property when initializing the Referral Component.